Cyber Security Consulting
3S Cyber Security
Everyone agrees Information is one of the biggest and most important assets. The information has to be protected to maintain trust with customers and maintain compliance with the governing organization. To defeat the attacker, an organization must be prepared and should implement the right set of strategies for managing processes, tools, and policies necessary to prevent, identify & detect, provide a response in a timely manner.

Cybersecurity is one of the most critical elements of corporate IT today, especially when companies are moving their business to the cloud, and sensitive data would be stored in the cloud. It is not the responsibility of cloud providers alone to provide the security of your data, but the responsibilities lie with each employee in the organization. Every organization must define robust cybersecurity policies and procedures that set the standards of behaviour for each employee in the organization. Good policies provide the guidelines for cybersecurity personnel to monitor, investigate, and manage risk. Key Challenges faced by companies today
- Access Controls
- Mobile Devices
- Unpatched Devices
- Cloud Applications
- Firewall Policies
- Monitoring
- Security Awareness Training
3S Information Security Solutions
At 3S, we believe in securing confidential data by implementing intelligent and systematic strategies by continuously integrating processes, people, and technology that protect vulnerabilities for your business and reduce security risks so you feel confident about the information being exchanged between internal or external sources.
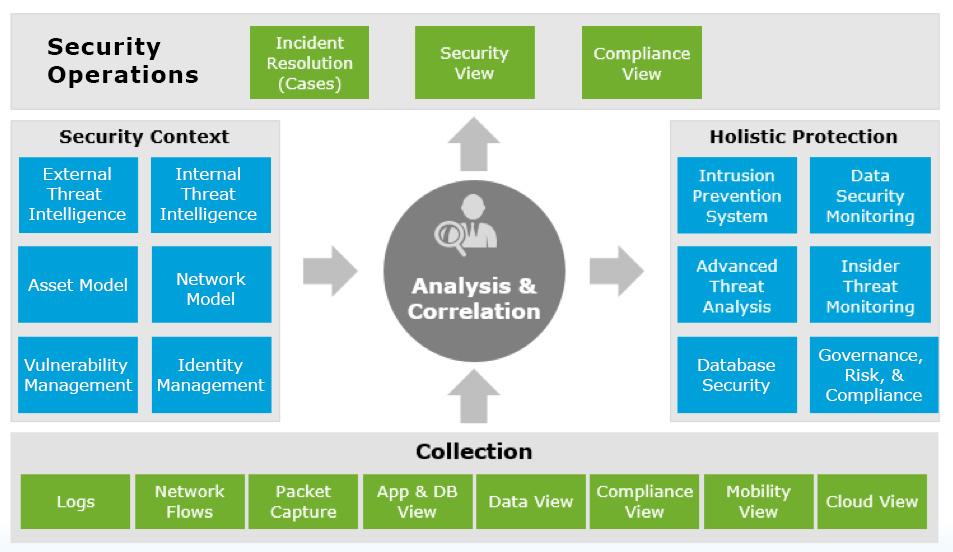
3S, as a leading security consulting organization, can help assess, define, design, implement, manage, and audit your organization’s cybersecurity policies on a regular basis. 3S will help safeguard the integrity of your systems & business while meeting compliance and regulatory requirements. Our organization has expertise in designing and implementing secure IT infrastructures that are compliant with GDPR, PCI-DSS, and HIPAA.
There are many simple, low-cost steps that 3S can help identify, assess, and manage cybersecurity risks in your organization. 3S experts will help evaluate threats and vulnerabilities based on the impact that they may have on the confidentiality, integrity, and availability of an organization’s assets.
Penetration Testing
 Organizations do all that they can to protect their critical cyber assets, but they don’t always systematically test their defenses.
Organizations do all that they can to protect their critical cyber assets, but they don’t always systematically test their defenses.
Penetration assessments – otherwise known as pen testing – are a type of ethical hacking that can be used to evaluate the security of a network regularly. Our team of highly-skilled cybersecurity experts utilizes a combination of tactical and strategic approaches to discover and exploit vulnerabilities in our clients’ Information Technology (IT) systems.
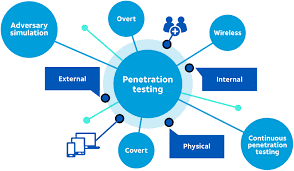 Our penetration assessments:
Our penetration assessments:
- Gather information about the target before the test (i.e., exploration)
- Identify possible entry points and attempt to break in
- Report the outcome through a detailed assessment document
Proprietary, Proven Tests
Average security companies often blur the lines between penetration tests and vulnerability assessments. At 3S, our proprietary pen testing methodology is based on years of experience in areas such as network administration, integration engineering, incident forensics, and response.
We combine penetration techniques with vulnerability assessment activities, configuration reviews, and architecture analysis. In some cases, we even evaluate policies and host interactive discussions with client staff members.
Whether we are testing an application or network environment, 3S’s pen testing will not only identify vulnerabilities, but it will also demonstrate them through exploitation – definitively determining if unauthorized access or other malicious activity is possible.
More Meaningful Results
In the hands of a 3S Pen Testing Expert, even limited penetration provides a more in-depth view of network and application interrelationships than any other company’s pen testing can.
We use pen testing as a tool to delve deeper into the systems and networks that need to be assessed. If our engineers find a weakness, we conduct a thorough review – checking details that would otherwise not be visible during a routine vulnerability assessment.
We examine how:
- Authentication and data traffic flows throughout the network, establishing the roles of various systems within the network
- Different systems support the business functions of the organization, recognizing what is important to whom
- Communication moves between a system and its users, giving us the vital information we need to design protective control mechanisms
By performing this thorough analysis, 3S can assign risk ratings to vulnerabilities, ensuring that our risk-remediation recommendations are cost-effective and appropriate for their environment.
Access Control
- Electronic
- Physical
Application
- Mobile
- Thick Client
- Web HTTP
- Web Services
Device
- Appliance
- Server/Work Station
Network
- External
- Internal
- Wireless
Are you ready to test your cyber defenses?
Contact 3S InfoSec
